Brute force attack mitigation - Account lockout counter and lockout duration
Account lockout policies, including parameters like account lockout counter and account lockout duration, are important security mechanisms that help mitigate brute force attacks by limiting the number of login attempts an attacker can make within a specified period. Unfortunately, if you are deploying a new 2016 / 2019 Active Directory Domain these are set to 0 (ZERO) so you must set those values appropriately in Group Policy.
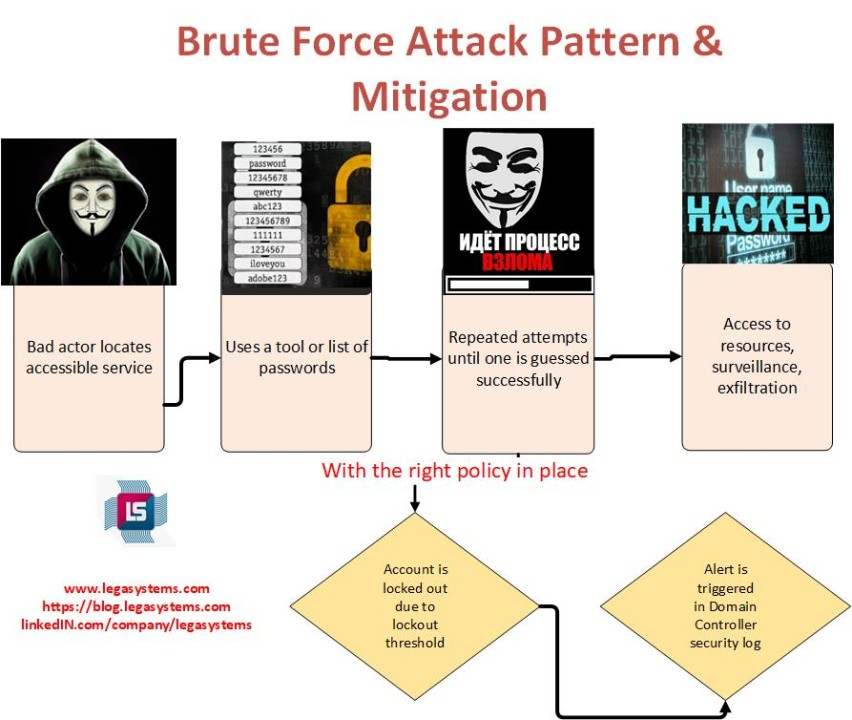
If you do not have an account lockout threshold and duration in place, an attacker can attempt an unlimited number of passwords until one is guessed right and you have been hacked. Proper threshold and duration policies will help mitigate this threat.

Here's how they work and why they are effective:
Account Lockout Counter:Definition: The account lockout counter, often referred to as the "threshold" or "retry limit," is the maximum number of consecutive failed login attempts that a user is allowed before their account is locked.How It Works: When a user attempts to log in and enters an incorrect password, the system keeps track of the number of failed attempts. If the number of consecutive failed attempts reaches or exceeds the account lockout counter, the account is locked or temporarily disabled.Mitigation of Brute Force Attacks: Brute force attacks involve an attacker trying numerous password combinations until they find the correct one. By limiting the number of attempts, account lockout policies make it extremely time-consuming and impractical for attackers to guess passwords through brute force. After a certain number of failed attempts, the account is locked, preventing further guesses.
Account Lockout Duration:Definition: The account lockout duration specifies how long an account remains locked after reaching the account lockout counter. During this time, the user is unable to log in.How It Works: Once an account is locked due to too many failed login attempts, it remains locked for the duration specified in the policy. After the lockout duration expires, the user can attempt to log in again.Mitigation of Brute Force Attacks: Account lockout duration serves as a deterrent to attackers. Even if they manage to reach the account lockout counter, they must wait for the lockout duration to expire before attempting further attacks. This delay makes brute force attacks less efficient and discourages attackers.
Here are some additional considerations:
Setting Appropriate Values: It's important to set reasonable values for the account lockout counter and lockout duration. If the threshold is set too low or the lockout duration is too long, it can inconvenience legitimate users. Conversely, if the threshold is too high or the lockout duration is too short, it may not provide adequate protection against attacks. If the values are not set at all, the brute force attacker can make an unlimited number of attempts once they are able to make tries through an accessible service.
Logging and Monitoring: Systems should log failed login attempts and lockout events for monitoring and investigation purposes. This helps in identifying potential attacks and unusual login patterns.
Password Policies: Account lockout policies should be part of a comprehensive password policy that encourages users to choose strong, unique passwords and change them regularly. I have another article that will walk you through this process.
Two-Factor Authentication (2FA): Implementing 2FA alongside account lockout policies can provide an additional layer of security. Even if an attacker guesses the password, they would still need the second factor to gain access.
Setting account lockout threshold and lockout period on a Windows Domain
You'll need to be a member of Domain Admins group in Active Directory and Group Policy management tools to configure these settings.
Open Group Policy Management:
On a Domain Controller go to Admin Tools > Group Policy management
Right-Click Default Domain Policy and choose Edit

Configure Account Lockout Policy:
In the Group Policy Management Editor, navigate to "Computer Configuration" > "Policies" > "Windows Settings" > "Security Settings" > "Account Policies."
Set Account Lockout Threshold:
Double-click on "Account Lockout Threshold" to edit the policy.
Specify the number of failed login attempts after which an account will be locked. For example, if you want to lock an account after 3 failed login attempts, enter "3."

Set Account Lockout Duration:
Double-click on "Account Lockout Duration" to edit the policy.

Specify the duration (in minutes) for which an account will remain locked after reaching the lockout threshold. For example, if you want accounts to be locked for 30 minutes, enter "30."

Set Reset Account Lockout Counter After:
Double-click on "Reset Account Lockout Counter After" to edit the policy.
Specify the duration (in minutes) for which the account lockout counter will be reset. This policy determines how long a user must go without failed login attempts before the counter is reset. Typically, it's a good practice to set this value to a higher value, such as "30 minutes" or "1 hour."
Apply the GPO:
Once you've configured the account lockout policies, close the Group Policy Management Editor.
The GPO will be applied to the domain if you made the Change in Default Domain Policy unless you have block inheritance checked.
Force Update or Wait:
You can force a Group Policy update on a specific computer by running the following command in Command Prompt with administrative privileges: gpupdate /force
What about Azure AD?
I've written a separate article on how to configure account lockout and threshold in Azure AD