Abstract
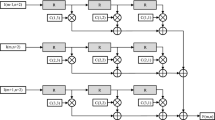
As a pivotal advance in the field of information security, steganography holds a crucial place in concealing sensitive information. It is the technique of hiding secret data within a digital media carrier, such as an image. An image steganographic scheme conceals secret data in a digital image by manipulating pixel values in a way that the data is undetectable to unauthorized parties in communication channels. These schemes are widely used for various real-time applications, including but not limited to content authentication, copyright protection, and biometric data protection. To effectively process image steganographic schemes in real-time applications, it is important to reduce computational delay and increase throughput. Implementing these schemes on a reconfigurable hardware platform is an efficient way to achieve these tasks. In this paper, we present a reconfigurable embedded system for an efficient steganographic scheme that embeds and recovers secret data in digital images using the AMD Xilinx Zynq-7000 all programmable system-on-chip (APSoC) platform. The system demonstrates real-time processing capabilities, delivering a frame rate of 30.7 FPS for a full high-definition RGB image, surpassing recent hardware implementations in terms of speed, resource utilization, and system throughput.



















Similar content being viewed by others
References
Amd xilinx: 7 series FPGAs data sheet: overview (DS180) (Accessed 03 April 2022). https://docs.xilinx.com/v/u/en-US/ds180_7Series_Overview
An introduction to AMBA AXI (Accessed 04 July 2022). https://developer.arm.com/documentation/102202/0200/AXI-protocol-overview
Exchangeable image file format - an overview | ScienceDirect Topics (Accessed 06 August 2022). https://www.sciencedirect.com/topics/computer-science/exchangeable-image-file-format
EXIF tags (Accessed 14 May 2022). https://exiftool.org/TagNames/EXIF.html
HTTP archive (Accessed 27 May 2022). https://httparchive.org/
Alarood, A., Ababneh, N., Al-Khasawneh, M., Rawashdeh, M., Al-Omari, M.: IoTSteg: ensuring privacy and authenticity in internet of things networks using weighted pixels classification based image steganography. Clust. Comput. 25(3), 1607–1618 (2022)
Ayyappan, S., Lakshmi, C., Menon, V.: A secure reversible data hiding and encryption system for embedding EPR in medical images. Curr. Signal Transduct. Ther. 15(2), 124–135 (2020)
Biookaghazadeh, S., Zhao, M., Ren, F.: Are FPGAs suitable for edge computing? In USENIX workshop on hot topics in edge computing (2018)
Chao, R.M., Wu, H.C., Lee, C.C., Chu, Y.P.: A novel image data hiding scheme with diamond encoding. EURASIP J. Inf. Secur. 2009(1), 1–9 (2009)
Elharrouss, O., Almaadeed, N., Al-Maadeed, S.: An image steganography approach based on k-least significant bits (k-LSB). In: 2020 IEEE international conference on informatics, IoT, and enabling technologies (ICIoT), pp. 131–135 (2020)
HajiRassouliha, A., Taberner, A.J., Nash, M.P., Nielsen, P.M.F.: Suitability of recent hardware accelerators (DSPs, FPGAs, and GPUs) for computer vision and image processing algorithms. Signal Process. Image Commun. 68, 101–119 (2018)
Hassaballah, M.: Digital media steganography: principles, algorithms, and advances. Academic Press (2020)
Hassan, F.S., Gutub, A.: Efficient image reversible data hiding technique based on interpolation optimization. Arab. J. Sci. Eng. 46(9), 8441–8456 (2021)
Hussain, M., Wahab, A.W.A., Idris, Y.I.B., Ho, A.T.S., Jung, K.H.: Image steganography in spatial domain: a survey. Signal Process. Image Commun. 65, 46–66 (2018)
Kumar, R., Jung, K.H.: Robust reversible data hiding scheme based on two-layer embedding strategy. Inf. Sci. 512, 96–107 (2020)
Kuo, W.C., Wang, C.C., Hou, H.C.: Signed digit data hiding scheme. Inf. Process. Lett. 116(2), 183–191 (2016)
Leng, H.S., Lee, J.F., Tseng, H.W.: A high payload EMD-based steganographic method using two extraction functions. Digital Signal Process. 113, 103026 (2021)
Liu, Y.X., Yang, C.N., Sun, Q.D., Wu, S.Y., Lin, S.S., Chou, Y.S.: Enhanced embedding capacity for the SMSD-based data-hiding method. Signal Process. Image Commun. 78, 216–222 (2019)
Lu, T.C.: Interpolation-based hiding scheme using the modulus function and re-encoding strategy. Signal Process. 142, 244–259 (2018)
Martelli, M., Dang, M., Seph, T.: Defining chaos. Math. Mag. 71(2), 112–122 (1998)
Menaka, D.R., Janarthanan, D.R., Deeba, D.K.: FPGA implementation of low power and high speed image edge detection algorithm. Microprocess. Microsyst. 75, 103053 (2020)
Menezes, A.J., Oorschot, P.C.V., Vanstone, S.A.: Handbook of applied cryptography. CRC Press, Boca Raton (2020)
Nawrocki, P., Pajor, J., Sniezynski, B., Kolodziej, J.: Modeling adaptive security-aware task allocation in mobile cloud computing. Simul. Model. Pract. Theor. 116, 102491 (2022)
Phadikar, A., Maity, G.K., Chiu, T.L., Mandal, H.: FPGA implementation of lifting-based data hiding scheme for efficient quality access control of images. Circuits Syst. Signal Process. 38(2), 847–873 (2019)
Qasaimeh, M., Denolf, K., Lo, J., Vissers, K., Zambreno, J., Jones, P.H.: Comparing energy efficiency of CPU, GPU and FPGA implementations for vision kernels. In: 2019 IEEE international conference on embedded software and systems (ICESS), pp. 1–8 (2019)
Qu, Z., Cheng, Z., Liu, W., Wang, X.: A novel quantum image steganography algorithm based on exploiting modification direction. Multimed. Tools Appl. 78(7), 7981–8001 (2019)
Ramalingam, B., Amirtharajan, R., Rayappan, J.B.B.: Stego on FPGA: An IWT approach. Sci. World J. : e192512 (2014). Publisher, Hindawi (2014)
Saha, S., Chakraborty, A., Chatterjee, A., Dhargupta, S., Ghosal, S.K., Sarkar, R.: Extended exploiting modification direction based steganography using hashed-weightage array. Multimed. Tools Appl. 79(29), 20973–20993 (2020)
Sathish Shet, K., Aswath, A.R., Hanumantharaju, M.C., Gao, X.Z.: Design and development of new reconfigurable architectures for LSB/multi-bit image steganography system. Multimed. Tools Appl. 76(11), 13197–13219 (2017)
Schneier, B.: Applied cryptography: protocols, algorithms, and source code in C. Wiley, India (2007)
Seyed Dizaji, S.H., Zolfy Lighvan, M., Sadeghi, A.: Hardware-based parallelism scheme for image steganography speed up. In: Gupta, D., Khanna, A., Bhattacharyya, S., Hassanien, A.E., Anand, S., Jaiswal, A. (eds.) International conference on innovative computing and communications, advances in intelligent systems and computing, pp. 225–236. Springer, Singapore (2021)
Shaik, A., V, T.: High capacity reversible data hiding using 2D parabolic interpolation. Multimed. Tools Appl. 78(8), 9717–9735 (2019)
Shet, K.S., Aswath, A.R., Hanumantharaju, M.C., Gao, X.Z.: Novel high-speed reconfigurable FPGA architectures for EMD-based image steganography. Multimed. Tools Appl. 78(13), 18309–18338 (2019)
Shivani, S., Patel, S.C., Arora, V., Sharma, B., Jolfaei, A., Srivastava, G.: Real-time cheating immune secret sharing for remote sensing images. J. Real-time Image Process. 18(5), 1493–1508 (2021)
Sinha, S., Goyal, N.K., Mall, R.: Reliability and availability prediction of embedded systems based on environment modeling and simulation. Simul. Model. Pract. Theor. 108, 102246 (2021)
Sinha Roy, S., Basu, A., Chattopadhyay, A., Das, T.S.: Implementation of image copyright protection tool using hardware-software co-simulation. Multimed. Tools Appl. 80(3), 4263–4277 (2021)
Spagnolo, F., Perri, S., Corsonello, P.: Design of a real-time face detection architecture for heterogeneous systems-on-chips. Integration 74, 1–10 (2020)
Standard, I.: Extensible metadata platform (XMP), ISO 16684-1:2012 (Accessed 27 April 2022)
Sun, J..y, Cai, H., Gao, Z..b, Wang, C..p, Zhang, H.: A novel non-equilibrium hyperchaotic system and application on color image steganography with FPGA implementation. Nonlinear Dyn. 111(4), 3851–3868 (2023)
Tyagi, S., Anurag, P., Pai, S.N.: Multilevel steganography for data protection. In: Hu, Y.C., Tiwari, S., Mishra, K.K., Trivedi, M.C. (eds.) Ambient communications and computer systems, advances in intelligent systems and computing, pp. 461–472. Springer, Singapore (2019)
Wang, X., Li, C., Song, J.: Motion image processing system based on multi core FPGA processor and convolutional neural Network. Microprocess. Microsyst. 82, 103923 (2021)
Wei, J., Quan, Z., Hu, Y., Liu, J., Zhang, H., Liu, M.: Implementing a low-complexity steganography system on FPGA. In: 2021 9th international conference on intelligent computing and wireless optical communications (ICWOC), pp. 64–68 (2021)
Wu, F., Zhou, X., Chen, Z., Yang, B.: A reversible data hiding scheme for encrypted images with pixel difference encoding. Knowledge-Based Syst. 234, 107583 (2021)
Zhang, R., Lu, C., Liu, J.: A high capacity reversible data hiding scheme for encrypted covers based on histogram shifting. J. Inf. Secur. Appl. 47, 199–207 (2019)
Zhang, X., Long, J., Wang, Z., Cheng, H.: Lossless and reversible data hiding in encrypted images with public-key cryptography. IEEE Trans. Circuits Syst. Video Technol. 26(9), 1622–1631 (2016)
Zhang, X., Wang, S.: Efficient steganographic embedding by exploiting modification direction. IEEE Commun. Lett. 10(11), 781–783 (2006)
Acknowledgements
This work was supported in part by the Natural Sciences and Engineering Research Council (NSERC) of Canada and in part by the Regroupement Strategique en Microelectronique du Quebec (ReSMiQ).
Author information
Authors and Affiliations
Contributions
All the authors conceived the idea. SH developed the theory and performed the experiments. All the authors verified the analytical methods, discussed the results and contributed to the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Harb, S., Ahmad, M.O. & Swamy, M.N.S. An efficient image steganographic scheme for a real-time embedded system and its hardware implementation on AMD Xilinx Zynq-7000 APSoC platform. J Real-Time Image Proc 20, 46 (2023). https://doi.org/10.1007/s11554-023-01302-x
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11554-023-01302-x